It is no longer a question, but a fact that the Internet is in the car. After discussing a number of useful mobile services in passenger cars, we have to conclude that our digital sovereignty will be lost if we do not take adequate measures.
Cars – the Ultimate Internet Frontier?
It is no longer a question, but a fact that the Internet is in the car. Already 15 years ago, luxury vehicles had been called “rolling computers”. By installing sensors and control units many useful driving functions such as parking a car, distance control, or autonomously braking in case of dangerous situations have been made available to the driver. Following the digital evolution, a number of projects have been kicked-off, which link the vehicle with the Internet and thereby create value-added services for navigation, map quality, emergency calls. However, even more business is expected from the development of new services, which combine vehicle data
- With infrastructure elements (e.g. lamp posts, induction loops, or traffic lights)
- With Internet data (e.g. stores, restaurants, traffic)
- With other vehicles
- And last but not least with passenger related data
Or which accumulate even more data of participating users/drivers/passengers to make more money. In particular the investments of companies such as Apple or Alphabet in the development of autonomous vehicles show these trends very clearly.
Many New Mobile Services Can Be Very Useful
Many of the available or planned mobile services in the vehicle offer useful, in some cases even life-saving functions, which will be useful for drivers and passengers. Deadly traffic accidents may be reduced, time spent in traffic jams can be used productively and minimized. Other features, however, are developed in the interest of Internet giants or car manufacturers. The data rights of drivers and passengers are ignored, their digital sovereignty is violated. In any case, clear data usage legislation is required. Unfortunately, we as passengers or drivers are not (yet?) aware of this or may be even negligent.
Some of these services are listed below with a discussion of relevant data, their origin, their ownership, and relevant actions for their protection.
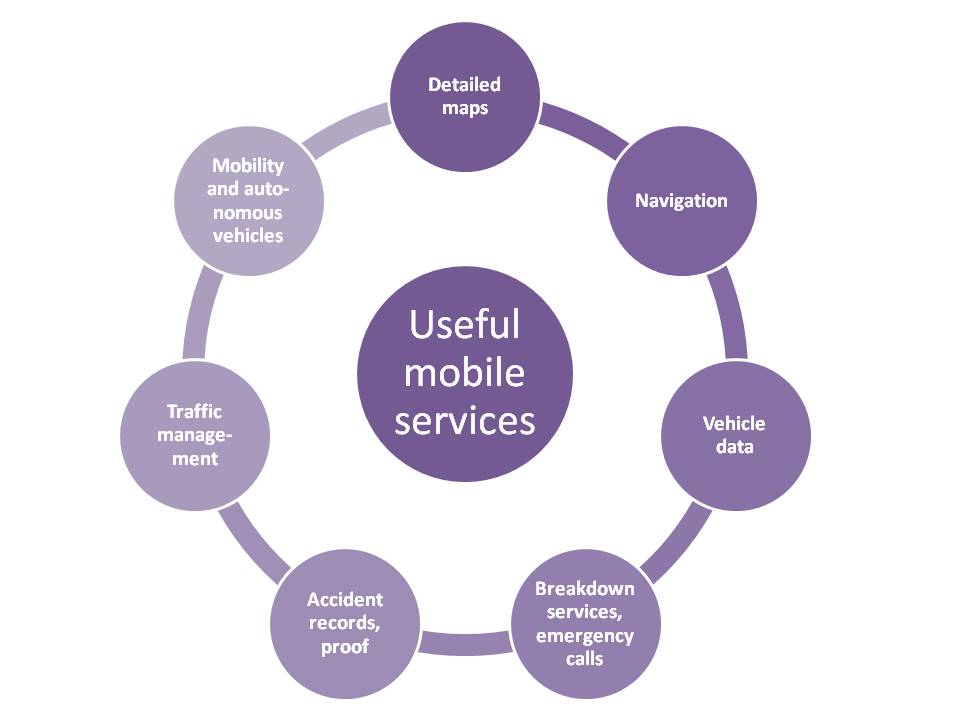
Mobility and autonomous driving are currently high potentials for fully changing the rules in the mobility arena. The driver role is eliminated and the car acts in a selfcontained way. All passengers in the car will be able to spend their time without paying attention to the traffic around them. The year of full autonomous driving is still under heavy debate, but the technical viability mid-term is out of question. Not only the car as a sign of individualism comes to an end. Mid- to long-term, transport related business models such as logistics, vehicle manufacturers, insurance, local and long-haul public transport will be measured in the mobility experience they offer to their customers. By optimizing transport flows a strong reduction of resource use (time, roads, gas and many more) is expected. The vehicles communicate between each other, with the road infrastructure and with traffic management systems in the backend. The mobility requirements of users are included in the selection of routes, transport means etc. Despite of the fact that some time will pass before this “vision” will be implemented, even today a number of important issues with respect to an individual’s digital sovereignty can be seen:
- During a ride a vehicle generates data related to the vehicle owner, at least to be able to bill the ride or to know who is responsible for damages.
- For integrating with the overall traffic and for optimizing routes and traffic flows, the vehicle requires access to other vehicles, to the road infrastructure, and to the traffic management system.
- Other data will be required for vehicle maintenance, service, or billing.
- When assigning the available data to individuals, mobility profiles will pop out automatically which may also be of interest for other services. And at the same time it can be used for monitoring individuals.
- If the vehicle does not belong to the „driven“ user, even more than today we need to clearly define who is the owner of the data generated during a ride and who is allowed to use the data respectively profit from the data use and at which costs.
- It must be defined, which data must be collected on a individual basis As much data as possible should be anonymized before their further use, so the originating individual cannot be identified.
The complete area of „Cyber Security“, mainly of the passengers, needs to be discussed somewhere else. How can one stop attacks in the car (bag with explosives left in a car), by the car (as an autonomous bomb), or on the car (by localizing the passengers)?
It is clear: Autonomous driving requires focused deliberation and research. As soon as available, we will include corresponding references to www.in4com.de pages.
Detailed and exact road maps are not only a requirement for having cars drive autonomously. By using car sensor data combined with location data, streets can be measured and the results can be fed back to the map data for optimized routing.
- We should ask: Who owns the sensor data – the drivers or the vehicle manufacturers? Must the driver make the data available to interested third parties and at which costs?
- Can resp. must the passenger data be separated from the geo-location data?
- What about third party data users such as insurance companies, Internet firms, advertising agencies, government – how do they get access to the generated data and at which costs?
Navigation is one of the most widely used services, which is derived by combining mobile devices and geo-location. Already today, be it in the car or on the phone, many useful functions are available: searching for empty parking, route, traffic information, the next sushi restaurant, and many more.
- Users make a multitude of personal data available, which are analyzed by service providers for different purposes and are often sold.
- Users have little or no control over the further use of their personal data by third parties – their digital sovereignty is simply ignored.
Currently, it seems, there is little or no sufficient understanding between information producers, information users/service providers, and regulators on an adequate business model. Data are used by service providers to optimize their business without regulation or control by the data owners.
- From the perspective of data sovereignty it is particularly questionable that the combination of a number of available data points (mash) can be used for user profiling. On the up-side, users can get help in routine jobs which cannot easily be done when driving a car. On the down-side, users’ liberty is at stake if is the service providers who decide which kind of information and functions is important for the users or what kind of data may be made available to other third parties. Contact services and car services have become "famous" for the unwanted behaviour of the corresponding service app operators.
- It should also be noted that the accumulated data at service providers is continuously at stake of being misused by attackers. We all know that the software used in today’s computer and cloud installations is not secure as Mark Goodman describes in “Future Crimes: Everything is Connected, Everyone is vulnerable and What We Can Do About It”, Doubleday, a division of Random House LLC, New York, 2015 (http://www.penguinrandomhouse.com/books/237130/future-crimes-by-marc-goodman/9780804171458; 2017-01-14, 20:55 GMT).
Vehicle information denotes such kind of information which is used by manufacturers for statistical purposes or which are directly linked with the operation of the car. Examples are maintenance data, management of recalls, software updates in the car, or customer binding campaigns. The expected increase of time share vehicles (such as car2go) is another reason for the manufacturer to collect detailed usage data. Customer identification may be required at least for service billing.
- Usually, drivers and passengers are the originators of vehicle data – in some cases, autonomous cars may drive from A to B without passengers, for example to refill the battery over night.
- Ownership of the generated data is not clarified today. The manufacturers see themselves as owners, even if most of the data is only generated in the combination with passengers.
- Data ownership may be defined by the usage model, but also by the car ownership model. Initially one may assume that buying a car implicitly makes the car owner also own the generated data. Manufacturers have to get buy-in from the car owner when further using the data. Unfortunately, this view is more the exception than the rule, as one can easily see in the legal notices of mobile phones.
- As in many other cases, from the point of view of data sovereignty it is time to act and clarify ownership of the data generated when driving. Clear regulation is required. Also, it has to be assured that personal data is separated from other data. Their correlation must only be possible based on a person’s buy-in or a court rule.
Emergency calls and help are functions, which are legally required in all new vehicles in the European Community from 2018 onwards. Their implementation requires the continuous monitoring of locations, information about the car’s passengers (e.g. via a camera), and details about the vehicle status. Communication via voice using microphone and speakers must be assured. The financial model of the service is yet to be defined. Car manufacturers try to compensate the costs for SIM cards, other vehicle components, and backend infrastructures by combining emergency services with other services paid by users.
- Data for the fast reaction in case of emergencies are generated in the vehicle, but they are due to a car’s passengers.
- Therefore, the passengers are owners of the data (if adequate regulation is in place).
- Usage rights for the generated data are not only with the owner, but also with those entities which take care of emergency calls according to legal requirements. Due to the specific nature of their work they should be under the same legal restrictions as doctors in a treatment of injured passengers.
- Relating vehicle data to the passengers should only be allowed if they have explicitly bought into it. Opting out any time must be possible. The emergeny function in the car cannot be sufficient to allow the generic use of personal data beyond the emergency response needs. The usage of such data must be restricted by law.
Analysis of accidents can be supported by the data stored by and in a vehicle. Court orders are required. The same proceedings as for private homes can be applied. The retrieved data can only be used for the purpose under scrutiny, other ways of usage are forbidden. The general availability of such data for other purposes (governmental or private businesses including manufacturers) should not be assumed.
Traffic flow management requires the combination and analysis of data from many sources: vehicle data, Internet, mobile devices, traffic or street infrastructure and potentially competing traffic management systems. The ultimate goal is the optimization of the mobility of all traffic participants and the required resources. A few examples shall demonstrate the complex situation.
- By smart management of traffic lights, jams can be reduced, the overall travel time of all mobile entities can be minimized, and last but not least the used resources (streets to be built and maintained, road deterioration, use of gasoline) can be restricted. To reach such goals, adequate information on the expected and actual traffic around the traffic lights must be available.
- Optimized routing combines information on the expected and actual traffic and navigates the users accordingly. Individual preferences can be taken into account.
- The overall resource consumption of a city to fulfil the mobility requirements of its citizens can be minimized without losing needs and wants of the participating individuals. Combined with autonomously driving vehicles, we have introduced the notion of the “individualized public transport”. The mobility requirements of the participating individuals at a certain time are required as input. Combined with actually available resources (e.g. roads, vehicles, parking lots, public transport), individual users can get the best route and means of transport according to their expectations.
Our Digital Sovereignty Gets Lost along the Way
A multitude of new, mobile services is linked to geo-location, which provides the most exact location of each individual at any time. Very often this is call a “security feature” which protects us from attacks or helps that we are found and rescued quickly. But is it not much more dangerous to be found anytime anywhere? Free, self-defined acts become impossible? Therefore, the digital sovereignty over geo-location data is highly important.
In the vehicle, the logging of car data is highly important and even becomes indispensible in an autonomous car. Similar to the black box of an airplane, the vehicle data are logged in detail and continuously and can be used, for example during the analysis of a traffic accident (velocity, steering activity, brake activities, driver reaction, environmental conditions, exact location). This implies the continuous monitoring of the driver/passenger at least as detailed as the pilot in the course of a flight. Pilots are responsible for the safety of the passengers they are flying and can be held responsible on a professional level. Do we have to request the same for the billions of drivers on the road? Also, the digital sovereignty over the vehicle data we generate must be specified and implemented effectively.
In order for the above examples to turn into reality, the number of required individual, personalized data are manifold. The data themselves are handled within a multitude of IT systems. For most of these operations, rules and measures to preserve digital sovereignty are yet to be set-up. Here we can see the close connection of mobility services to other services such as finance, health care, and others.
Secure Your Digital Sovereignty And Stay Mobile!
Securing and safeguarding your digital sovereignty all by yourself is limited to a certain extent. Firstly, often it is not clear that our data can be used or processed by third parties. Secondly, even if we understand the many ways our data are used (based on the terms of use we all do not read anyway), we could do little. Due to unavailable alternatives we typically have to accept terms of use as set-up by the provider of a service. For example, you have to accept the terms of use for any Android/Apple/Windows10 phone in order to be able to use it. – otherwise we would have bought an expensive, but useless piece of aluminum. Thirdly, even we actively reduce the amount of data being sent across the network, there will remain a residual minimum amount, e.g. for billing (one of the German anti-terror rulings was to require name and address of the owner of a prepaid card). The linkage between a phone and its owner allows many insight views of a user’s behavior and interests. But even without name, address, or telephone number users in many cases can be uniquely identified by their phone’s or computer’s configurations and configuration parameters, as shown in a project at the University Erlangen Nuremberg.
Nevertheless, we should continuously ask ourselves,
- Which of my data must be stored in the cloud?
- Which private details do I show in social networks?
- Which apps/applications do I really need?
- What does an app do with my data/why does it need so many?
- Can I restrict or manage an app’s data hunger, e.g. using the phone’s or computer’s operating system?
- Are there similar apps, may be at some costs, which can do with less data?
- What are the terms of use of an app or a cloud storage provider? Such are often hidden behind the “protection of user data”.
- Can I restrict/manage the forwarding of my data by apps?
- Are my data encrypted during transfer or when stored remotely?
- Can I surf the Web anonymously (mostly terrorists or criminals know seem to use such tools).
- Can I use different identities when working on the net?
- Can I conceal my identity?
Of course, then you need to act according to your answers to the questions above.
However, in order to be able to execute the right of digital sovereignty legal requirements and their implementation are a must. In parallel legal specifications, awareness must be established with our political representatives that digital sovereignty is an important and foundational right. This requires educational campaigns for politicians and all civilians. Consumer associations can play an important role in this, as well as civil right organizations or computer science experts and established data protection agencies and institutions. All these organizations should be involved in the wording of required law. Important scientific work has already been done (see for example the work on the data protection model in Germany). Major resistance should be expected as today’s “data users” are belonging to important international players (monopolies). They are able to spend nearly unlimited resources and expertise to stop the implementation of effective consumer protection legislation.
Looking at the growing number of interfaces to the Internet and of information becoming public by the introduction of new gadgets (home surveillance, body sensors and many more), 100% data sovereignty may not be achievable. There will remain some residual risks – and may be an insurance for it. Stay alert!
